Is A Private Key Required For Sha256 Hash Generator
From a private key to a public key. As Wikipedia tells us a ECDSA private key is just the scalar product of a private key (the secret exponent) and the curve – secp256k1 for Bitcoin – base point. How to do that is complex, but let’s just take it for granted, as you’ll either use a. Generate a SHA-256 hash with this free online encryption tool. To create a SHA-256 checksum of your file, use the upload feature. To further enhance the security of you encrypted hash you can use a shared key. HMAC user-input keys that are longer than the specific hash algorithms blocksize are first shortened. (By running the long keys through the hash. And then using that hash as the actual key.) SHA256 outputs 256 bit hashes. That's 32 bytes. So I suggest you generate 256 bit HMAC secret keys. (Using a cryptographically secure random generator.). Generate the SHA256 hash of any string. SHA256 Hash Generator. This online tool allows you to generate the SHA256 hash of any string. SHA256 is designed by NSA, it's more reliable than SHA1. Enter your text below: Generate. Password Generator.
- Is A Private Key Required For Sha256 Hash Generator Free
- Is A Private Key Required For Sha256 Hash Generator Parts
- Is A Private Key Required For Sha256 Hash Generator Download
- Is A Private Key Required For Sha256 Hash Generator For Mac
- Is A Private Key Required For Sha256 Hash Generator For Sale
This free SHA256 online generator allows you to generate a SHA256 (32-byte) hash of any string or input value, which is then returned as a hexadecimal number of 64 digits.
SHA-256 is a member of the SHA-2 cryptographic hash functions designed by the NSA. SHA stands for Secure Hash Algorithm. Cryptographic hash functions are mathematical operations run on digital data by comparing the computed 'hash' (the output from execution of the algorithm) to a known and expected hash value, a person can determine the data's integrity. A one-way hash can be generated from any piece of data, but the data cannot be generated from the hash. (BitcoinWiki)
SHA-256 or SHA-2 is the modern cryptographic standard for online security. The algorithm produces an almost-unique, fixed-size 256-bit (32-byte) hash value. It is usually represented as a hexadecimal number of 64 digits.
.It is suitable for password validation, challenge hash authentication, anti-tamper, digital signatures, etc. SHA-1 and SHA-2 are two different versions. They differ in both constructions and in the bit-length of the signature. SHA-2 is one of the successor hash functions to SHA-1 and is one of the strongest hash functions available. SHA-256 is not much more complex to code than SHA-1 and has not yet been compromised in any way.
The basic idea behind cryptographic hashing is to take an arbitrary block of data and return a fixed “hash” value. It can be any data, of any size but the hash value will always be fixed.
- The hash functions must be computationally efficient. It is very important because if the computer processes a cryptographic hash function and receive the output in a very long period of time it will not be very practical. To be useful, hash functions must be computationally efficient.
- The most important idea about the hash function is that the output must not reveal any information about the input. This is called pre-image resistance. The cryptographic hashing algorithms can receive any kind of input. The input can include numbers, letters, words, or punctuation marks, a single character, a sentence from a book, a page from a book, or an entire book. The fixed output guarantees the security because if a longer input produced a longer output, then attackers would already have a seriously helpful clue when trying to discover someone’s private input. In addition, changing one character in a long string of text must result in a radically different digest. If a cryptographic hash function produced different outputs each time for the same input was entered, it would be against the whole point of hash functions.
- The hash function must have collision resistance meaning that it must be impossible to find two different inputs that produce the same output.
- Cryptographic hash functions must be deterministic. In other words, for any given input, a hash function must always give the same result. If you put in the same input a hash function must produce the same exact output. As mentioned above, the inputs to a hash function can be of any length. This means there are infinite possible inputs that can be entered into a hash function. Hash functions are part of information security methods. A hash function is simply a function that takes in input value and creates an output value deterministic of the input value. For any x input value, you will always receive the same y output value whenever the hash function is run. The best way to demonstrate hash function is with a modular function which is also called modular arithmetic or clock arithmetic. Modular functions are mathematical functions that, put simply, produce the remainder of a division problem.
The SSL industry uses SHA-2 as its hashing algorithm for digital signatures.
The SHA-2 hash function is implemented in some widely used security applications and protocols, including TLS and SSL, PGP, SSH, S/MIME, and IPsec.
The SSL/TLS protocol enables secure transmission of data from one device to another across the internet. The SSL provides authentication. But the SSL/TLS protocol facilitates a connection using asymmetric encryption. This means there are two encryption keys that each handle one half of the process: a public key for encryption, and a private key for decryption. Every SSL certificate contains a public key that can be used by the client to encrypt data, and the owner of said SSL certificate securely stores a private key on their server which they use to decrypt that data and make it readable.
From 2016, SHA-2 is used as a hashing algorithm for digital signatures. SSL/TLS certificate uses that signature. SHA-2 will likely remain in use for at least five years. However, some unexpected attack against the algorithm could be discovered which would prompt an earlier transition.
A larger bit hash can provide more security because there are more possible combinations. But if two different values or files can produce the same hash, a collision will occur. Collisions are extremely dangerous because they allow two files to produce the same signature, thus, when a computer checks the signature, it may appear to be valid even though that file was never signed.
The SHA-256 is used in the bitcoin network.
The SHA-256 algorithm supports the Bitcoin network. Since this hash function is one way it works perfectly for cryptocurrency and namely - Bitcoin.
The SHA-256 takes part in the mining process. The process of releasing new coins and introducing them into the current supply is called mining. Mining is performed by powerful computers that solve cryptographic tasks. It ensures that the network is secure and no hackers can interrupt the process or falsify payments.
Bitcoin uses the SHA-256 algorithm two times, which is called double-SHA-256. This is how the formula looks like:
Previous Block Hash = SHA-256(SHA-256(Block Header))
The merkle root is also created by SHA-256 and placed into the block header. A Merkle root is the hash of all the hashes of all the transactions that are part of a block in a blockchain network. In other words, it stores the data about all transactions performed in the network.
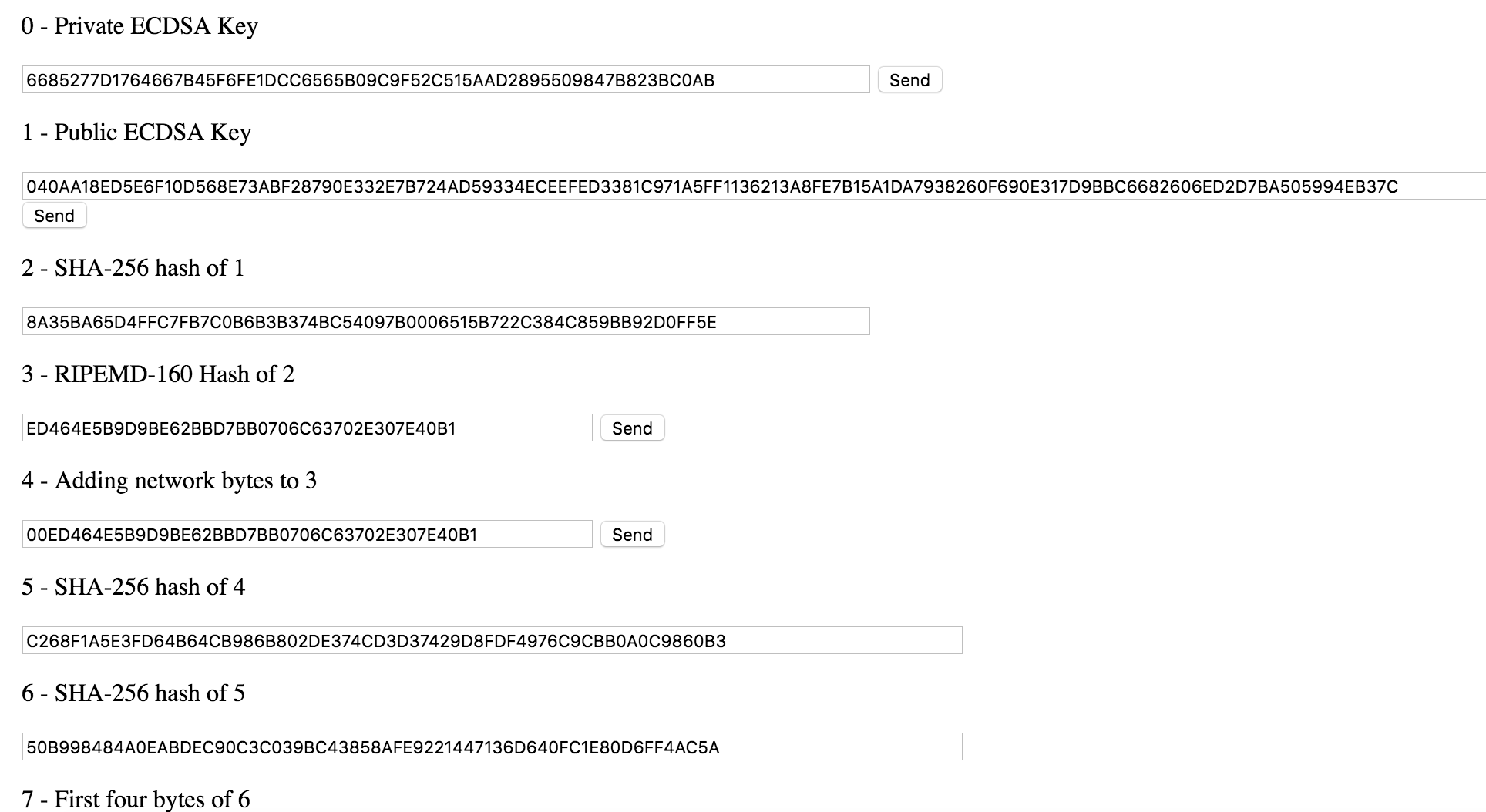
SHA-256 also takes part in the creation of Bitcoin addresses which are known as private keys and required to perform transactions between users. The address is a unique code that consists of random numbers. The created key should go through two algorithms – SHA-256 and RIPEMD160.
These two algorithms create an opportunity to create short private keys. If the public key includes 256 bits, the private one includes only 160 bits. This was made easier for the users to operate with shorter addresses.
What is a Private Key?
A private key is a secret 256-bit long number randomly selected when you create a Bitcoin wallet. This is the address which enables you to send the Bitcoins to a recipient’s address. You never share the private key to anyone.
The number and type of cryptographic functions implemented for security reasons defines just how random and unique the key is.
A private uncompressed key always begins with a 5 and it looks like this:
5Hwgr3u458GLafKBgxtssHSPqJnYoGrSzgQsPwLFhLNYskDPyyA
What is a Public Key?
A public key is another address consisting of numbers and letters which is a derivate from private keys after they have been encrypted via the use of mathematical functions. The encryption process cannot be reversed and thus no one can find out the original private key. This is the address that enables you to receive Bitcoins.
The hash of a public key is always 1:
1BvBMSEYstWetqTFn5Au4m4GFg7xJaNVN2
This address you publicly make available in order to receive Bitcoins. There is no limit to how many public addresses a user can generate. In order to generate such a key and subsequently a wallet address, there have to be applied a number of conversions to the private key. These conversions are known as hash functions, which are un-reversible conversions.
Creating a Public Key with ECDSA
The first thing you have to do is apply to your private key an ECDSA, also know as Elliptic Curve Digital Signature Algorithm. An elliptic curve is defined by the equation y² = x³ + ax + b with selected value for a and b. There is an entire family of these curves which can be applied. Bitcoin makes use of the secp256k1 curve.
Applying an ECDSA to the private key will result in a 64-byte integer composed of two 32-byte integers put together which represent the X and Y of the point on the elliptic curve.
Below is the code you would require in Python language:
private_key_bytes = codecs.decode(private_key, ‘hex’)
# Get ECDSA public key
key = ecdsa.SigningKey.from_string(private_key_bytes, curve=ecdsa.SECP256k1).verifying_key
key_bytes = key.to_string()
key_hex = codecs.encode(key_bytes, ‘hex’)

In the code presented above the private keys were decoded with codecs. As in Python, there are at least two classes that can keep the private and public keys, “str”, a string array, and “bytes”- a byte array, things can get a little confusing.
This is because an X string array is not equal to an X byte array, but it equals the byte array with two elements, O<. The codecs.decode method converts a string into a byte array.
After applying ECDSA, we will have to add the bytes 0x04 (04 as a prefix) to the resulted public key. This will generate a Bitcoin full public key.
Compressing the public key
Instead of using the long version of the public key we can compress it to be shorter.
This is done by taking the X from the ECDSA public key and adding 0x02 if the last byte of Y is even, and the 0x03 byte if the last byte is odd.
Encrypting the Key with SHA-256 And RIPEMD-160
Now we move on to create our wallet address. Regardless of the method applied to the public key, the procedure is the same. Obviously, you will have different resulting addresses.
For this, we will need to apply two hash functions: first, we apply SHA-256 to the public key, and then encrypt the result using RIPEMD-160. It is very important that the algorithms are applied in this exact order.
At the end of this process, you will have a 160-bit integer which represents an encrypted public key.
Below is the code needed to encrypt the public key in Python:
public_key_bytes = codecs.decode(public_key, ‘hex’)
# Run SHA-256 for the public key
sha256_bpk = hashlib.sha256(public_key_bytes)
sha256_bpk_digest = sha256_bpk.digest()
# Run RIPEMD-160 for the SHA-256
ripemd160_bpk = hashlib.new(‘ripemd160’)
ripemd160_bpk.update(sha256_bpk_digest)
ripemd160_bpk_digest = ripemd160_bpk.digest()
ripemd160_bpk_hex = codecs.encode(ripemd160_bpk_digest, ‘hex’)
Adding the network byte
As Bitcoin has two networks, main and test, we will need to create an address which will be used on the mainnet. This means that we will have to add 0x00 bytes to the encrypted public key. For testnet use, you would have to add 0x6f bytes.
Calculating the Checksum
The next step is to calculate the checksum of the resulted mainnet key. A checksum ensures that the key has still maintained its integrity during the process. If the checksum does not match, the address will be marked as invalid.
In order to generate a key’s checksum, the SHA-256 hash function must be applied twice and then take the first 4 bytes from this result. Keep in mind that 4 bytes represent 8 hex digits.
The code required for calculating an address checksum is:
# Double SHA256 to get checksum
sha256_nbpk = hashlib.sha256(network_bitcoin_public_key_bytes)
sha256_nbpk_digest = sha256_nbpk.digest()
sha256_2_nbpk = hashlib.sha256(sha256_nbpk_digest)
sha256_2_nbpk_digest = sha256_2_nbpk.digest()
sha256_2_hex = codecs.encode(sha256_2_nbpk_digest, ‘hex’)
checksum = sha256_2_hex[:8]
Now the last step required to make an address is to merge the mainnet key and the checksum.
Encoding the Key with Base58
You will notice that the resulted key does not look like other BTC addresses. This is because most convert them to a Base58 address.
Below is the algorithm needed to convert a hex address to a Base58 address:
def base58(address_hex):
alphabet = ‘123456789ABCDEFGHJKLMNPQRSTUVWXYZabcdefghijkmnopqrstuvwxyz’
b58_string = ‘’
# Get the number of leading zeros
Teamviewer 8 license key generator. leading_zeros = len(address_hex) — len(address_hex.lstrip(‘0’))
# Convert hex to decimal
address_int = int(address_hex, 16)
# Append digits to the start of string
while address_int > 0:
digit = address_int % 58
digit_char = alphabet[digit]
Is A Private Key Required For Sha256 Hash Generator Free
b58_string = digit_char + b58_string
address_int //= 58
# Add ‘1’ for each 2 leading zeros
Is A Private Key Required For Sha256 Hash Generator Parts
ones = leading_zeros // 2
for one in range(ones):
b58_string = ‘1’ + b58_string
return b58_string
The resulted string will represent a compressed Bitcoin wallet address.
Is A Private Key Required For Sha256 Hash Generator Download
Conclusion
Is A Private Key Required For Sha256 Hash Generator For Mac
The process of generating a Bitcoin wallet address from a private key is not that difficult if you pay close attention to the aforementioned steps.
Is A Private Key Required For Sha256 Hash Generator For Sale
If your private key is full or compressed, the resulting addresses will look different, but both of them are just as valid.